Zero Trust Security
Zero Trust is a security framework based on the principle of “never trust, always verify.” Unlike traditional perimeter-based security, Zero Trust assumes that threats exist both inside and outside the network, requiring strict identity verification for every user, device, and application attempting to access resources.
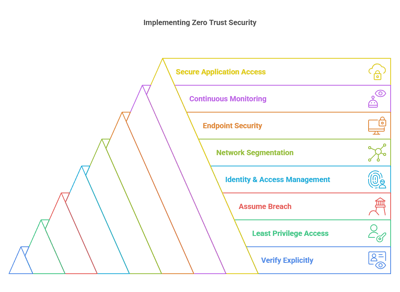
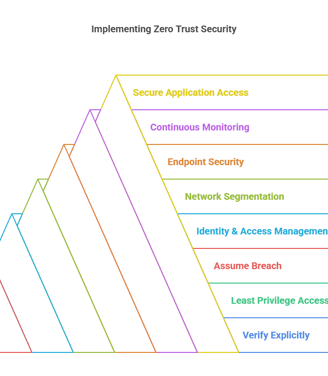
Core Principles of Zero Trust
1. Verify explicitly - Authenticate and authorize every access request based on identity, device health, and context.
2. Least Privilege Access - Grant users and devices only the minimum permissions needed to perform tasks.
3. Assume Breach - Design security to limit lateral movement and contain potential threats.
Best Practices for Implementing Zero Trust
1. Identity and Access Management (IAM)
Enforce multi-factor authentication (MFA) for all users.
Implement role-based access control (RBAC) to restrict permissions.
Continuously monitor and log access attempts for anomalies.
2. Network Segmentation & Micro-Segmentation
Divide networks into smaller, isolated segments to prevent lateral movement.
Apply strict access controls between segments, even within internal networks.
3. Endpoint Security
Ensure all devices meet security standards before granting access ( device posture checks ).
Use endpoint detection and response (EDR) to monitor and mitigate threats.
4. Continuous Monitoring & Analytics
Deploy AI-driven behavioral analytics to detect suspicious activity.
Use real-time threat intelligence to respond to emerging risks.
5. Secure Application Access
Replace VPNs with Zero Trust Network Access (ZTNA) for secure remote access.
Encrypt all data in transit and at rest.
6. Automation & Policy Enforcement
Automate security responses (e.g., revoking access upon detection of anomalies).
Enforce dynamic policies that adapt to risk levels (e.g., stricter verification for sensitive data).
Benefits of Zero Trust
Reduces Attack Surface – Limits unauthorized access.
Improves Compliance – Meets regulatory requirements (e.g., GDPR, NIST).
Enhances Visibility – Provides real-time monitoring of all access requests.
Supports Remote Work – Secures hybrid and cloud environments.
Adopting Zero Trust for Future-Proof Security
Zero Trust is not a one-time project but an ongoing strategy. Organizations must continuously assess risks, update policies, and integrate new technologies to stay ahead of evolving threats.
Trust nothing. Verify everything.


Get in touch


Get in touch
83 Watsonbrook Dr. Brampton, L6R 0R5, ON, Canada
contact@aidoctrine.com
Shahed Tower, 10 Floor, Mirgab, Kuwait city, Kuwait
